Contents
MFA - mandatory for Admins
On Friday 8th September, we will be introducing some new security measures to Identity.
In our continuous effort to increase security measures and enhance data protection, we will be implementing changes to how multi-factor authentication (MFA) is managed. Should you have any questions or require assistance, our Customer Success and Support teams are available to help.
Please note, the changes outlined below will also apply to test accounts.
Here's a breakdown of the upcoming changes.
MFA required for admins
Identity / MyWorkplace admin users will be required to use MFA if not logging in using federated credentials.
Starting 8th September, all users with Customer or User admin roles within Identity / MyWorkplace will be required to use MFA when logging in, unless they are using federated credentials to authenticate. This enhancement is a proactive measure to ensure the highest level of security for accounts with elevated privileges.
If you authenticate using a federated identity provider (such as Azure AD or Okta Identity), you will not experience any change to your login process. The seamless integration with these identity providers will continue to provide a hassle-free experience.
You can start using MFA sooner than 8th September if you wish, ask another Customer or User admin in your organisation to edit your user account and turn on the Requires MFA setting. When you next log in, you'll be asked to set up MFA. You can see what those steps look like here and you can check our MFA FAQs for admins here.
Paired account credentials only
For users who have already paired a federation account with their Advanced account, the 'federated only' option will be enabled. Moving forward, these users will only be able to log in using the credentials of their paired federation account (such as Azure AD or Okta Identity). This means that using Advanced credentials for login will no longer be an option for users with paired federation accounts.
Depending on your federation settings, your users may see both the federation and Identity authentication options on the login screen. You can hide the Identity login option to make this clearer for your users, as if they try to use the Identity option they will get a message saying 'Incorrect username or password'.
To do this, go to your federation settings and make sure Always on is enabled. This will take users directly to your identity provider authentication screen after they have entered their email address.
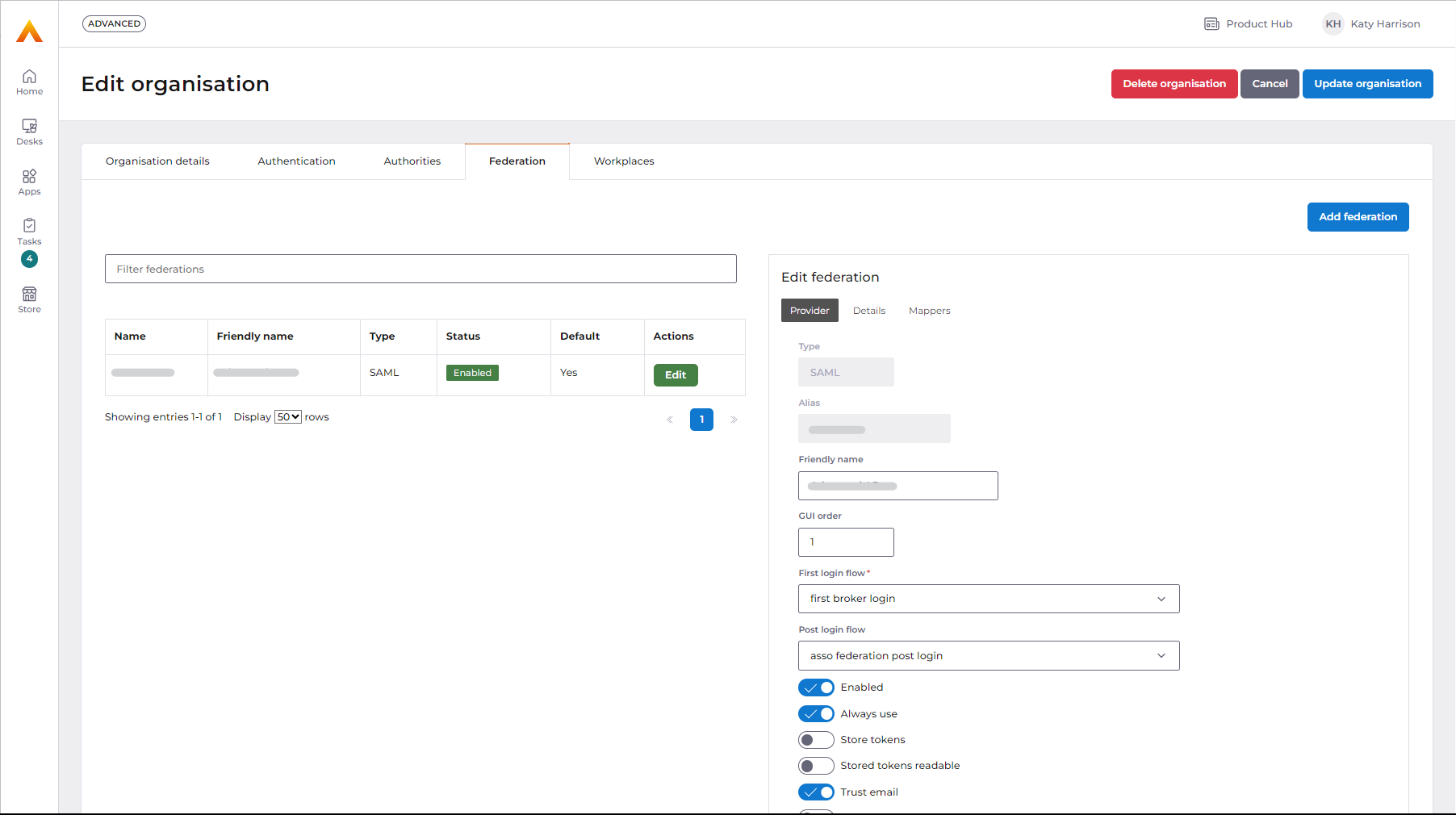
Before - login screens when federation is not set to always on

Once the user enters their email address, they are shown a screen with both the federation authentication option if they have a paired account, and Identity authentication.

User has to select the federation option, shown here as Azure AD. If they try to enter a username or email and password on this screen they will get a message saying 'Incorrect username or password'.
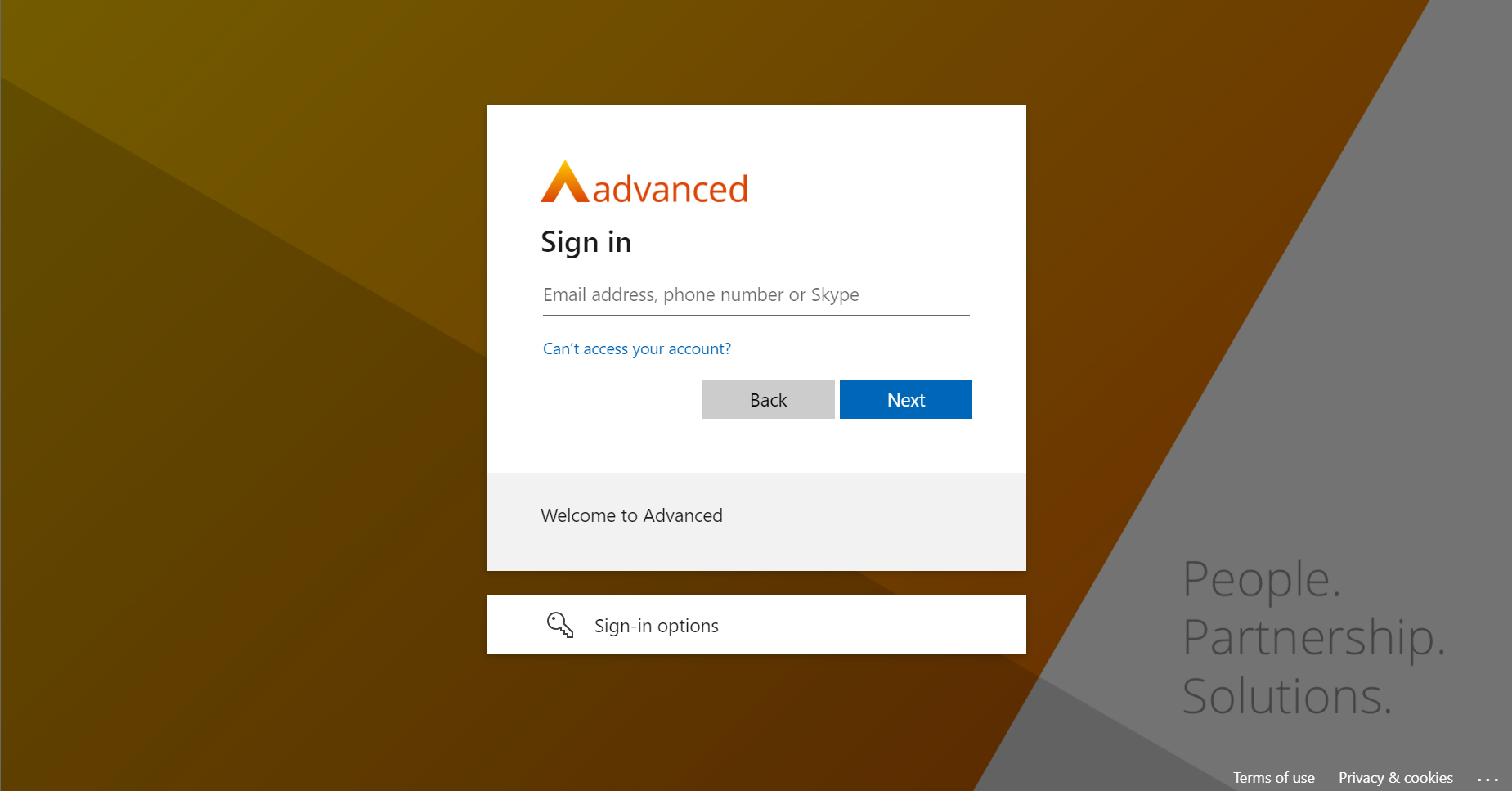
After - login screens when federation is set to always on

User enters their email address and is taken straight to your identity provider authentication.
Change to MFA disable option
When you enable MFA with Identity for either your organisation or individual users, the option to directly disable MFA will no longer be available.
Keeping MFA enabled provides an extra layer of security that aligns with industry best practices. By maintaining a consistent MFA requirement, we can ensure a higher level of protection for your accounts and sensitive data.
If you ever need to deactivate MFA after it has been enabled, please submit a request to your OneAdvanced Support team. They will review your request and work with you to ensure that proper security measures are in place before making any changes to your MFA settings.