Identity
Admins
Federated authentication
Making sure your users only use federated single sign-on to authenticate
Federating Identity with Azure Active Directory
How to add or replace an x509 certificate for Azure Active Directory federations
Configuring multi-factor authentication (MFA)
Identity and MFA FAQs for admins
Password policy
Resetting passwords
User roles and permissions
Creating and managing users
Onboarding new users with welcome emails
Adding custom content to welcome emails
Creating and managing custom scopes
Add Login URLs to your Organisation
MFA - mandatory for Admins
Unlock user account
Setting up a SAML Client
An Introduction to Multi-Factor Authentication & Single Sign-On
Identity and MFA FAQs
OneAdvanced Single Sign-on login process when using an authenticator app
OneAdvanced Single Sign-on login process when using email for authentication
OneAdvanced Single Sign-on login process for federated accounts
OneAdvanced Identity login using username
User Journey for EasyPass (Passkeys)
Security questions
How to help keep your OneAdvanced account safe and secure
Integrations
OneAdvanced AI
Getting started
Introducing OneAdvanced AI
How does OneAdvanced AI work?
Benefits of using OneAdvanced AI
Limitations of using OneAdvanced AI
Definition of terms
Prompts
Getting started with prompts in OneAdvanced AI
Prompt engineering
Avoiding Common Pitfalls and Errors
Using Prompts in OneAdvanced AI
Using OneAdvanced AI to Summarise a Document
Using OneAdvanced AI to Simplify Information
Using OneAdvanced AI to Compare Documents
Using OneAdvanced AI to Create Visuals Using Data
Private Spaces
Intelligent Chat Agents
Introducing Intelligent Chat Agents
Accessing Intelligent Chat Agents
Using Intelligent Chat Agents
Intelligent Chat Agents Catalogue
Administration
FAQs
Web Search
Platform
Helpful how-to guides
How To - Add a Spreadsheet or Chart to your Desk
How To - Add Youtube Videos to a Desk
How To - Add a Spotify Playlist to a Desk
How To - Add Microsoft Stream Videos to a Desk
How to stop unwanted time-outs
Admin
Desks
Applets
Applets Overview
Advanced Financials Applets
Setting up Advanced Financials Applets
Advanced HR Applets
Clear Review Applets
Contract Management Applets
Countdown Applet
Desk Notes Applet
iFrame Applet
My Link/Links Applet
RSS Feed Applet
Ideas Applets
Tasks
Data Platform
Data Platform FAQs
Data Platform (Bring Your Own BI/Data Share) - Connection Options
Data Platform (Bring Your Own BI/Data Share) - User Licence Assignment Administration
Data Platform (Bring Your Own BI/Data Share) – How to Connect Microsoft Power BI to OneAdvanced Data Platform
Data Platform (Bring Your Own BI/Data Share) - Snowflake ODBC Connector Configuration Guide
Data Platform (Bring Your Own BI/Data Share) - Connecting Microsoft Excel to Snowflake Using ODBC
OneAdvanced Mobile app
How to install the OneAdvanced mobile app on your device
Instructions: Adding OneAdvanced Mobile App to Microsoft Intune Company Portal
Licencing
- All topics
- Identity
- Admins
- Federated authentication
- How to add or replace an x509 certificate for Azure Active Directory federations
How to add or replace an x509 certificate for Azure Active Directory federations
These steps will show you how to add an x509 certificate for your Azure Active Directory (Azure AD) federation or how to replace your current x509 certificate if your existing one is going to expire.
- In Azure AD, navigate to Enterprise applications on the left-hand side navigation.
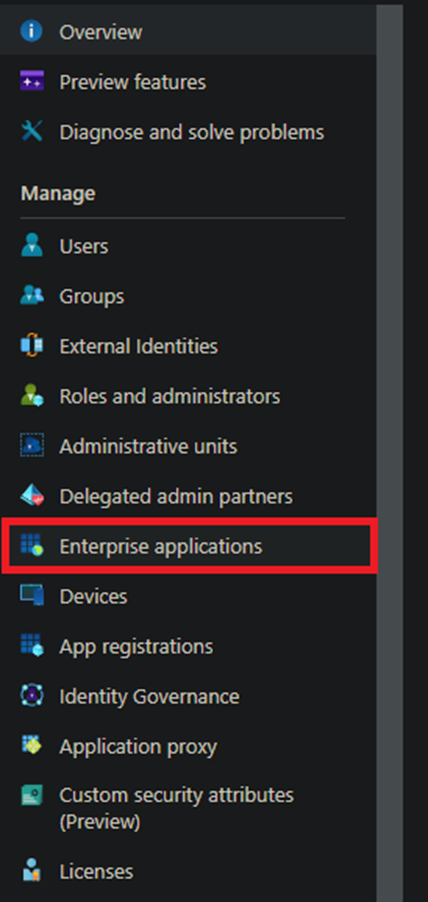
- Choose the Enterprise application that you want to require signature verification for.
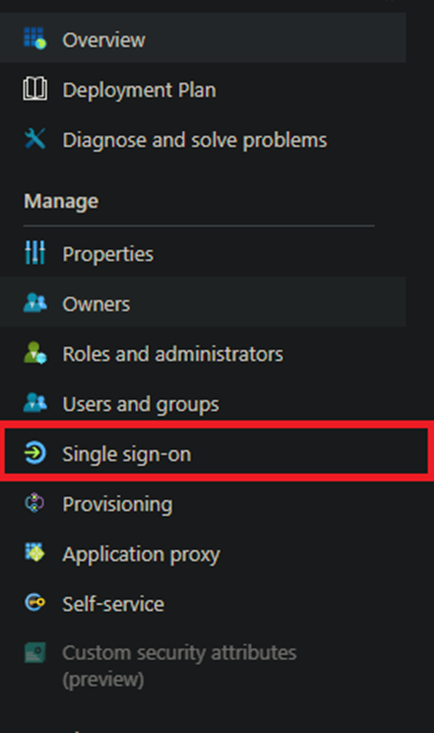
- Select Single sign-on on the left hand side bar navigation.
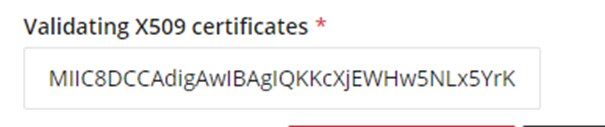
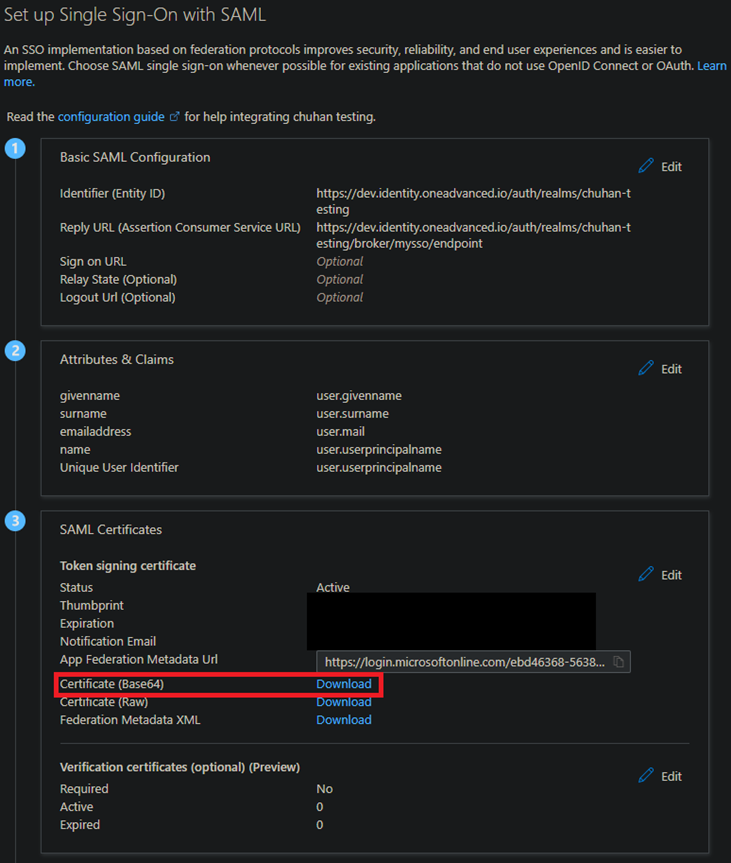
- Within the SAML Certificates section, press download next to “Certificate (Base64)”.
- Navigate to the folder where the certificate has downloaded to, right click on the file and open it with Notepad. Delete the section that reads "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----".
On the second line with the text, press the backspace button so that the line moves up one. Repeat this for each of the lines beneath until you have one joined sentence.
Before changes:

After changes:

Copy the text that is left on the file as you will need it later.
- Head to MyWorkplace and navigate to Organisations, which can be located in Apps under System settings. Select the organisation that has the Azure AD federation configured.
Select the federation tab, select the federation that you wish to configure if it is pre-existing and then select the Details tab within.
- Make sure the following toggles are set to enabled:
✅ HTTP-POST binding response
✅ HTTP-POST binding for AuthnRequest
✅ Want assertions signed
✅ Validate signature
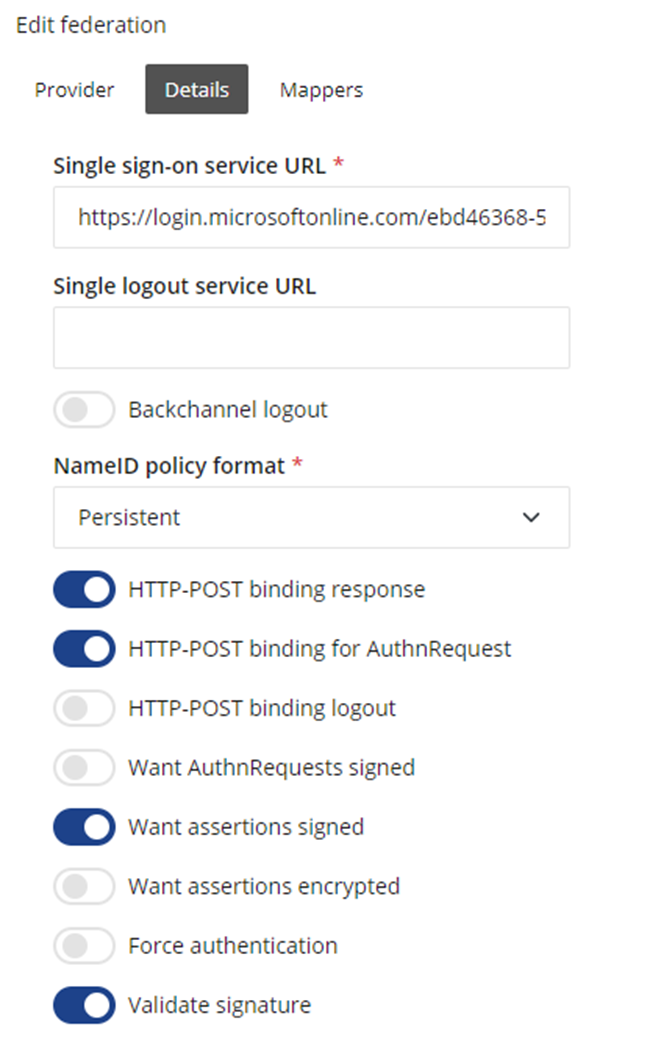
- Paste the value that you copied earlier into the text field and press save federation on the top right.